Securing Remote Desktop Protocol (RDP) with Advanced MFA on Windows Platforms
Remote Desktop Protocol (RDP) provides essential access for IT teams to manage and support Windows devices and servers. However, RDP’s ubiquity as a service running on TCP port 3389 also makes it a prime attack vector for cybercriminals seeking to infiltrate networks through stolen credentials or brute force. Applying advanced multi-factor authentication (MFA) solutions to gate RDP connectivity significantly reduces this threat landscape.
This article explores best practices and technologies for hardening RDP access protection, including risk-based authentication policies, conditional access rules, single sign-on (SSO) integration, session monitoring, and other layers that complement core MFA security.
RDP Attack Vectors and Credential Compromise Risks
Before examining how to secure RDP connectivity, it’s important to understand what makes it a target:
- Weak passwords vulnerable to brute forcing credentials
- External exposure increasing attack surfaces
- Lateral movement to access internal resources once logged in
- Difficulty tracking potential insider misuse
Attackers steal user credentials through phishing campaigns or by capturing hashes, enabling remote access without additional factors challenged to verify identity.
Integrating Advanced MFA Policies for RDP
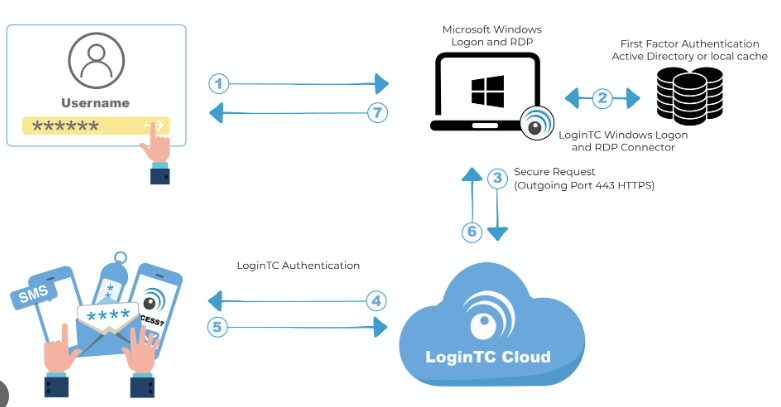
Applying advanced MFA frictionlessly prompts for an additional factor during the RDP windows logon sequence while allowing seamless access for approved users under normal conditions.
Modern solutions can step up baseline legacy MFA with functionality like:
- Adaptive authentication driven by AI/ML risk signaling
- Automated user behavior analytics baselining
- Active directory synchronization
- Single sign-on (SSO) for simplified login flows
- Custom endpoint agents enforcing MFA policies
This maintains both security and productivity for administrators legitimately utilizing RDP for tasks like desktop support, server maintenance, and patching activities.
Manage Access with Allow Listing
- Create IP allow lists of trusted office locations and ranges of managed devices permitted to connect via RDP
- Configure RDP settings and firewall policies to only allow connections from the defined allow lists
- Automatically update allow lists if new company subnets are added or device ranges change
- Test RDP connectivity after applying allow lists to ensure legitimate access isn’t disrupted
Enable MFA for Privileged Access
- Categorize accounts into standard and privileged admin access levels
- Exempt standard users from blanket MFA requirements if operational challenges arise
- Mandate MFA specifically for elevated admin accounts like domain admins or server operators
- Require administrator accounts to use hardened credentials policies separate from standard employees
Block Brute Force Attackers with Custom Policy
- Set failed attempt thresholds before automatic account lockouts (e.g. 10 failures)
- Define and tune timeframes for counting failed attempts (e.g. 10 in 5 minutes)
- Determine lockout duration once threshold reached (e.g. account locked for 15 minutes)
- Configure IP banning after a number of account lockouts to block systematic attacks
Reset Encryption Levels and Protocols
- Review currently utilized TLS/SSL encryption protocols for RDP sessions
- Prohibit outdated SSLv2/SSLv3 and early TLS 1.0/1.1 versions still allowing connections
- Enforce updated TLS 1.2+ cipher suites providing robust encryption
- Enable Network Level Authentication (NLA) providing certificate pre-authentication
Couple MFA to Session Privilege Level
- Integrate MFA with a Privileged Access Management (PAM) solution
- Step up identity verification if admin commands attempted mid-session
- Allow standard RDP usage like system monitoring without repeated MFA prompts
- Scope underlying session policies to Windows services and resources accessed
Govern Access with Conditional Rules
- Define signals like unfamiliar endpoints or atypical geo-locations
- Limit frictionless access only from managed devices or internal networks
- Require MFA spontaneously if anomalous signals detected during login
Mask RDP Servers with Gateway
- Obscure direct visibility of RDP servers through firewall policy
- Install bastion forest server to route connections through dedicated gateway
- Enforce security monitoring, logging, and scan detection at perimeter
Monitor Live Sessions for Risk Signals
- Track real-time RDP user activity after sessions initiated
- Detect potential compromise through behavioral analysis
- Enable rapid response like session termination or account suspension
Secure Web Client Gateways
- Support browser-based remote desktop clients alternatives through web portal
- Integrate robust MFA during initial gateway authentication stage to harden risk surface
On-Premises vs. Cloud Deployment Models
- Evaluate integration requirements with existing on-premises infrastructure
- Determine if a cloud platform enables easier long-term management
- Assess availability of hybrid models deploying cloud MFA gateways with on-prem agents
Windows RDP Integration Methods
- Review if native or open-source RDP libraries are leveraged
- Validate plugin, agent, or API integration mechanisms
- Test ease of rollout with current Windows OSes and Server versions
Flexibility of Policy Engine
- Automate policy triggers for contextual, adaptive step-up
- Check ability to scope controls to user groups
- Confirm simple customization for different usage, risk patterns
Self-Service User Enrollment
- Evaluate convenience of end-user registration options
- Verify accessibility of instructions and documentation
- Pilot ease of use with less technically-skilled employees
Contextual Signals for Adaptive Policies
- Catalog breadth of signals from endpoints, behaviors, anomalies
- Test accuracy of risk scoring algorithms during simulations
- Tuning false positives if friction triggered incorrectly
Active Session Controls
- Session recording, termination, and user detail visibility
- Integrate privileges management for inline command oversight
- Confirm tooling aligns to internal response workflows
Access Analytics and Reporting
- Dashboards centralizing auth event logging
- Flexible filtering on failure reasons, user metrics
- Data integration into security information management stack
Infrastructure, Resources, and Scalability Needs
- Choose simplest integration complexity for current Windows stack
- Size platform based on admin user counts needing RDP MFA
- Scale up signals, policies, and analytics over time
On-Premises vs. Cloud Deployment Models
- Evaluate integration requirements with existing on-premises infrastructure
- Determine if a cloud platform enables easier long-term management
- Assess availability of hybrid models deploying cloud MFA gateways with on-prem agents
Windows RDP Integration Methods
- Review if native or open-source RDP libraries are leveraged
- Validate plugin, agent, or API integration mechanisms
- Test ease of rollout with current Windows OSes and Server versions
Flexibility of Policy Engine
- Automate policy triggers for contextual, adaptive step-up
- Check ability to scope controls to user groups
- Confirm simple customization for different usage, risk patterns
Self-Service User Enrollment
- Evaluate convenience of end-user registration options
- Verify accessibility of instructions and documentation
- Pilot ease of use with less technically-skilled employees
Contextual Signals for Adaptive Policies
- Catalog breadth of signals from endpoints, behaviors, anomalies
- Test accuracy of risk scoring algorithms during simulations
- Tuning false positives if friction triggered incorrectly
Active Session Controls
- Session recording, termination, and user detail visibility
- Integrate privileges management for inline command oversight
- Confirm tooling aligns to internal response workflows
Access Analytics and Reporting
- Dashboards centralizing auth event logging
- Flexible filtering on failure reasons, user metrics
- Data integration into security information management stack
Infrastructure, Resources, and Scalability Needs
- Choose simplest integration complexity for current Windows stack
- Size platform based on admin user counts needing RDP MFA
- Scale up signals, policies, and analytics over time
The Critical Role of MFA in Any RDP Security Strategy
As modalities for remote work and cloud consumption continue expanding, the ubiquity of RDP across Windows environments makes it a prime target for endpoint and network infiltration. While Microsoft has added protections like Network Level Authentication and CredSSP encryption by default, credential theft and brute forcing risks remain without robust identity and access management.
Implementing advanced MFA solutions creates consistent identity verification challenges before clients establish RDP sessions, dramatically reducing reliance on basic login credentials vulnerable to compromise. MFA also enables tighter conditional controls and session policies while allowing approved users unimpeded access to facilitate IT support and servicing capabilities.
By combining multi-factor authentication prompts with complementary practices like allow listing authorized IPs, watchlisting high-risk users, and actively monitoring live connections, organizations can embrace RDP confidently while closing dangerous security gaps.
As remote connectivity becomes the rule rather than the exception for both employees and IT teams, securing access with MFA provides necessary assurances against even sophisticated identity deception and theft tactics.
Conclusion
RDP will continue serving as a linchpin protocol across Windows environments, but leaves windows open for exploitation if legacy authentication dependencies remain in place. Advanced MFA solutions applying context and risk-based analysis give security teams confidence they can enable RDP without reservations.
Integrating adaptive authentication requirements secures each stage of the RDP session lifecycle while allowing transparent access for managed company endpoints under normal conditions. Just as MFA has broadly reduced risk across cloud services and VPN connections, its capabilities provide similar protection and oversight essential for harnessing RDP safely.
FAQs
Q: Does enabling Network Level Authentication protect RDP without MFA?
A: While NLA improves security, authentication still depends on easily stolen or guessed credentials vulnerable to replay attacks. MFA blocks breach reliance.
Q: Can conditional access rules be set at the command level within RDP sessions?
A: Yes, some advanced MFA platforms allow policies triggering additional authentication factors if privileged actions are attempted within live RDP connections.
Q: What’s the most convenient form of MFA for securing RDP access?
A: Transparent methods like push notification authentication maintain productivity without disrupting workflows for legitimate login attempts.
Q: Is MFA equally important for both internet-facing and internal RDP endpoints?
A: Yes, as compromised user credentials can enable unauthorized access to internal resources if RDP sessions aren’t properly guarded at all entry points.
Q: Can RDP sessions be encrypted end-to-end if MFA is enabled?
A: Yes, MFA simply provides identity verification prior to establishing connectivity. Session encryption depends on policies like NLA and TLS versions configured.

Kaushal Joshi is a versatile author with expertise in web development and technical writing. With a passion for both coding and effective communication, Kaushal has forged a dynamic career at the intersection of technology and content creation. His proficiency in web development is complemented by a talent for articulating complex technical concepts in clear and accessible language. Through his writing, Kaushal not only contributes to the evolving field of web development but also empowers readers with the knowledge to navigate the digital landscape. His commitment to bridging the gap between technology and understanding makes Kaushal Joshi a respected figure in both the web development and technical writing communities.
Leave a Reply